In an age dominated by technology, privacy concerns are at an all-time high. Many individuals believe they can manage their information effectively. They seek control over what is shared and with whom. However, this belief often proves to be an illusion. It can feel as if choices made in the digital realm are genuine, but the reality presents a more complex picture.
Every click, every preference, and every purchase contributes to a vast web of profiles. Companies utilize this wealth of information to tailor their marketing strategies, often without explicit consent. Consumers may attempt to withdraw from these practices, hoping to regain their sense of autonomy. Yet, an underlying truth remains: exit strategies rarely lead to complete detachment.
Despite efforts to minimize exposure, remnants of personal data linger. Deleting accounts or opting for privacy settings sometimes seems ineffective. The persistence of digital footprints complicates the quest for genuine privacy. Ultimately, individuals wrestle with the paradox of choice while navigating an intricate landscape of surveillance and marketing.
Understanding this dynamic is crucial in a world where information reigns supreme. It reveals how entangled personal choices can become in the hands of unseen entities. As technology evolves, the quest for true independence from pervasive systems may appear increasingly elusive. Awareness can empower individuals to make informed decisions, yet the challenge remains. It's a delicate balance between the desire for privacy and the practicalities of modern existence.
The Opt-Out Illusion
In today’s digital landscape, the impact of online activities affects nearly everyone. Individuals often believe they have control over their personal information. However, the reality is more complicated. Even when users think they have opted out of sharing, their data may still be exploited in various ways. This pervasive reach can shape experiences and decisions without individuals realizing it.
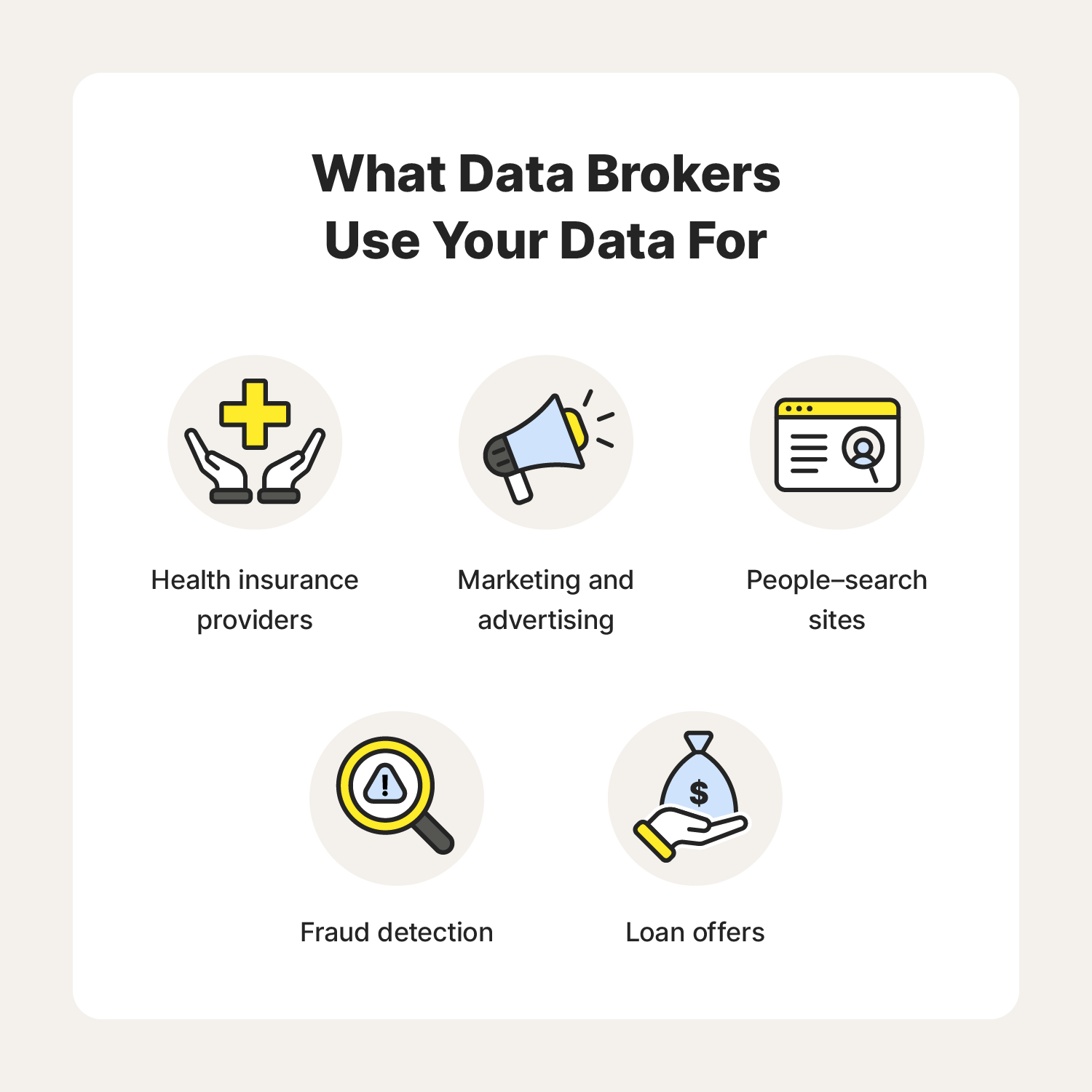
Understanding how these entities operate requires digging deeper into their strategies. They collect information through various means, often unobtrusively. Here are some common methods they employ:
- Web tracking tools that monitor online behavior.
- Social media activity that reveals personal interests.
- Mobile applications that access location and usage patterns.
- Public records that provide insights into demographics.
Each of these techniques contributes to a larger picture, often without user consent. While individuals may feel they are protecting their information by opting out, the underlying mechanisms remain intact. This means that even with attempted precautions, significant data can still be gathered and analyzed.
Moreover, the landscape is constantly evolving. New technologies and methods emerge that further complicate privacy concerns. When a person unchecks a box or opts for a privacy setting, they might believe they are safeguarded. However, hidden layers of data collection often persist. It creates a false sense of security.
In many cases, people are unaware of how deeply their information is integrated into broader systems. This integration leads to targeted advertising, personalized content, and other practices that can feel intrusive. The cycle reinforces itself: users make choices based on presented information, while those in control profit from hidden data exchanges.
To navigate this complex environment, awareness is crucial. Recognizing the methods employed by companies can empower individuals to take more informed actions. As technology advances, staying educated about rights and protections is essential for safeguarding personal privacy in a realm where informed consent is often sidelined.
Understanding Data Brokers’ Influence
In today’s interconnected world, personal information is a valuable commodity. Individuals often underestimate how much control others have over their private details. The influence of these entities extends beyond mere marketing strategies. Their reach penetrates various aspects of life, often unnoticed. Many people navigate life blissfully unaware of the extent of surveillance.
As technology has advanced, so has the sophistication of methods used to gather information. This collection occurs through various channels, from online activities to offline behaviors. Subtle cues, such as browsing history and purchase patterns, contribute to a comprehensive profile. These profiles inform not just advertisements. They affect employment opportunities, credit scores, and even insurance rates.
Such pervasive monitoring can feel overwhelming. Most individuals believe they have a degree of privacy, yet, this belief is misplaced. It's crucial to recognize how deeply integrated these practices have become in daily life. The consequences are often far-reaching, shaping not only choices but perceptions of identity.
What begins as simple data collection morphs into a powerful influence on personal narratives. Companies capitalize on the knowledge they possess to target users with tailored communications. As a result, it creates an environment where consent feels almost obligatory. Furthermore, the blurring of lines between user agency and corporative interests complicates matters.
Understanding this dynamic is essential. With awareness comes the power to make informed decisions. Each click, each interaction contributes to an invisible ledger that records preferences and behaviors. The relationship between consumer and corporation is no longer straightforward; it is layered and intertwined. Knowledge of this reality is the first step toward reclaiming agency in an increasingly data-driven society.
The Reality of Data Privacy
In today's interconnected world, the concept of privacy is increasingly complicated. Many believe that opting out of data collection grants them a sense of security. However, the truth is far more complex and nuanced. With each online interaction, personal information is often collected, analyzed, and shared without explicit consent. It's a web of transactions that feels overwhelming yet familiar.
People often think that simply opting out of services or platforms protects their information. Yet, this is not the case. Even with the best of intentions, choices made in the digital landscape rarely guarantee real protection. Privacy settings may offer comfort but can be misleading. One might feel a false sense of control while unknowingly exposing themselves to potential risks.
Moreover, the technological advancements make it incredibly easy to gather data. Information flows in ways that can be invisible to the average user. Social media, mobile apps, and websites are constantly monitoring user behavior, creating profiles that might not even match reality. It's a dance of algorithms and analytics that many are unaware of.
While laws and regulations exist to protect personal information, gaps remain. There is a significant disparity between what consumers believe they are safeguarding and what is happening behind the scenes. Many individuals feel powerless against the forces that shape their digital footprint, leading to growing anxiety about their online presence. Trust is a fragile concept in this ecosystem.
Ultimately, navigating the terrain of privacy requires knowledge. Understanding the mechanisms of data collection is the first step toward empowerment. People should strive to remain informed about the intricacies of their online interactions. This awareness can pave the way for more intentional choices regarding personal information, enabling individuals to reclaim some semblance of control over their digital identities.
Challenges of Opting Out

In a world where personal privacy seems increasingly elusive, individuals often grapple with the complexities surrounding their online presence. Many believe that opting out of certain services or data collection practices can provide relief. However, the reality is more convoluted. Choices made in an attempt to regain control often lead to new challenges. The landscape of privacy is riddled with pitfalls that make this endeavor far from straightforward.
Firstly, the sheer number of platforms and services complicates the process. Each site implements its own protocols for opting out. Moreover, users must navigate various settings to achieve the desired level of privacy. This task can become overwhelming quickly. For many, it feels like a never-ending battle against an invisible force.
While some platforms offer an easy way to withdraw consent, others employ intricate methods that obscure the process. Difficulty in locating the right options can lead to frustration. Furthermore, even when users successfully opt out, their data might still be collected through indirect channels. This situation highlights the deceptive nature of consent mechanisms available online.
Legally, individuals may believe they are protected, yet loopholes exist within existing regulations. These gaps allow companies to exploit users’ personal information without their explicit agreement. As a result, navigating through the maze of consent becomes increasingly daunting. Despite their best efforts, many individuals feel defeated by this complex framework.
Moreover, the burden of keeping track of changes to policies falls on users themselves. A change in terms of service can mean that previous choices are rendered moot. This constant flux is frustrating, especially when one aims to maintain privacy. Consequently, staying informed requires continual vigilance, which is often unrealistic in today’s fast-paced environment.
Ultimately, while attempting to reclaim control over personal information may seem achievable, the practical challenges involved create significant hurdles. Issues of accessibility, legal ambiguities, and the dynamic nature of digital policies contribute to an uphill battle that leaves many feeling lost. Consequently, the journey to safeguard privacy often becomes a paradoxical struggle between awareness and helplessness.
The Role of Consumer Consent
In the world of information sharing, consent is often considered a cornerstone of ethical practices. Each individual holds a certain level of authority over their personal information, or at least, that's how it seems. However, the reality is far more complicated. Many are unaware of what they truly agree to when they sign up for services. It’s essential to understand that consent is not just a formality; it can have significant implications for privacy and security.
Most users believe that they have a clear understanding of consent. Yet, many aspects go unrecognized. For instance, fine print in agreements often hides critical information. Users might click "agree" without fully comprehending the consequences. This disconnect contributes to the challenges surrounding information privacy.
Moreover, consent can be misleading, as it often implies a choice when, in fact, options may be limited. In many cases, consumers feel they have no alternative but to accept certain conditions. This situation puts individuals in a precarious position, where their personal information can be leveraged with little regard.
| Consent Type | Description |
|---|---|
| Explicit Consent | Clear agreement to specific actions regarding personal information. |
| Implicit Consent | Assumed agreement based on actions or circumstances. |
| Informed Consent | Agreement based on full knowledge of the implications involved. |
Understanding these nuances highlights how consent varies. Furthermore, it emphasizes the importance of being informed before making agreements. Individuals must critically evaluate what they are approving. Unfortunately, many do not take the time to do so, leading to unintentional permission for widespread information distribution.
Thus, consumer consent in the context of information sharing is more than a simple checkbox. It encompasses a complex web of expectations, comprehension, Explore more on Medium and consequences. Striking a balance between personal choice and informed decision-making is essential. In a rapidly evolving digital landscape, awareness and education are key to navigating the intricate dynamics of consent.
Data Collection Techniques Explained
In today’s digital landscape, various methods are employed to gather personal information. Understanding these techniques is essential for anyone concerned about their privacy. Each approach is designed to collect insights about individuals, often without their knowledge. This incessant tracking takes place across multiple platforms and devices.
Cookies and tracking pixels are among the most common tools. They silently record user activities online, creating a detailed profile. Furthermore, social media platforms utilize sophisticated algorithms to analyze user interactions. This practice enables targeted advertising and personalized content delivery.
Additionally, mobile applications frequently request access to personal data. Users, eager to download the latest app, often grant permissions without a second thought. Location tracking can reveal daily routines, shopping habits, and even spending patterns. In essence, this information becomes a valuable commodity for those who know how to leverage it.
Surveillance technologies, such as facial recognition and geolocation services, present another layer of complexity. These systems can track individuals in real-time, providing a granular view of their movements and interactions. This data is not merely collected for fun; it plays a critical role in shaping marketing strategies and enhancing user experiences.
The aggregation of this information leads to the creation of comprehensive profiles. These profiles are then utilized by businesses, often without explicit consent from individuals. While users might feel a sense of control, the reality remains that their information flows into a vast ecosystem, where it is analyzed, sold, and repurposed.
Understanding these collection methods empowers individuals to make informed choices. Knowledge is power, especially when navigating a world filled with potential privacy pitfalls. Being aware of how personal information is harvested can spark important conversations about user rights and data ownership.
Legal Protections and Their Limitations
The landscape of privacy laws is complex and often confusing. Many individuals believe their personal information is secure. However, the reality can be quite different. Various laws exist, yet they frequently fall short in practice. Protecting personal information can feel like an uphill battle.
Legislation aims to safeguard user privacy and restrict unauthorized access. Frameworks such as GDPR and CCPA represent significant advancements. Yet, these protections are not foolproof. They offer varying degrees of security based on jurisdiction and applicability. Enforcements can be inconsistent, leaving loopholes for exploitation.
Understanding the challenges associated with legal frameworks is crucial. Compliance can burden organizations, leading to unintended risks and oversights. Regulations often lack clear definitions, creating ambiguity in interpretation. Consequently, businesses may exploit these gaps. This can result in personal data being mishandled without consequence.
Moreover, individuals may find it difficult to assert their rights. Not everyone knows how to access their data or challenge violations. Legal jargon can be intimidating, discouraging victims from seeking justice. Even when they do pursue action, the process can be lengthy and fraught with obstacles. Consequently, many people remain unaware of their options, leading to feelings of helplessness.
Ultimately, while laws exist to protect privacy, their limitations are substantial. Enforcement might vary significantly across regions and sectors. As technology evolves, so do the tactics employed by those amassing personal information. Continuous adaptation of policies is necessary but often slow. Without consistent updates, legal protections may lag behind technological advancements.
In conclusion, although there are measures in place, significant gaps persist. Awareness of these limitations empowers individuals to advocate for stronger protections. Active engagement in privacy discussions can drive change. Only then can a more secure environment for personal information be established.
Impact on Personal Identity and Security
Modern society increasingly intertwines with technology, leaving individual identities more vulnerable. Personal information, once private, is now often exposed and exploited. This shift raises urgent questions about how we protect ourselves. Security breaches are becoming commonplace, and the consequences can be devastating.
Privacy erosion impacts more than just personal data. It affects how individuals perceive themselves and interact with the world. The fear of surveillance looms large. Each click, each like, each comment contributes to an ever-expanding digital footprint.
Consider the myriad of potential risks:
- Identity theft can lead to financial ruin.
- Data leaks may expose sensitive information, jeopardizing personal safety.
- Manipulation through targeted advertising can influence decisions, shaping behaviors subtly.
- Loss of anonymity fosters a culture of conformity, discouraging free expression.
As social media and online services continue to thrive, users often unwittingly surrender their autonomy. However, many do not fully understand the implications of their choices. Information compiled by companies creates detailed profiles that can be sold, traded, or misused. Such practices can distort personal identity, reducing individuals to mere data points. It becomes crucial to recognize that privacy is not an abstract concept; it directly impacts personal security and agency.
In addition, data collection practices often go unnoticed, complicating comprehension of one's online presence. Individuals tend to underestimate how much information is out there. For instance, various applications and websites track behaviors, preferences, and even locations, all while users remain oblivious to their scope. This can lead to a false sense of security, as trusting platforms may inadvertently share data with third parties.
Ultimately, understanding the risks is vital in today's digital landscape. Each decision regarding information sharing carries weight, influencing not just personal security but also one's identity. As technology evolves, so must our approach to safeguarding our privacy. Awareness and proactive measures can mitigate some risks, empowering individuals to take control of their online personas.
Strategies for Minimizing Data Exposure
In today’s digital landscape, protecting personal information has become more crucial than ever. Individuals often find themselves exposed to various entities seeking to gather their details. With every click, every scroll, and every share, data can be harvested in ways that feel invasive. Thankfully, there are practical measures that can be taken to enhance privacy and mitigate the risks associated with information leakage.
First, awareness of privacy settings across different platforms is essential. Social media, online services, and apps frequently provide customizable options to control what is shared. Regularly reviewing these settings allows users to tighten their grip on their information. Also, consider utilizing privacy-oriented alternatives for search engines and browsers. Tools like these help to limit tracking activities.
Employing virtual private networks (VPNs) can provide an additional layer of protection. VPNs encrypt internet traffic, making it more challenging for unwanted parties to monitor online activities. Moreover, being mindful of the permissions granted to applications can drastically reduce unnecessary data sharing. Always ask: does this app really need my location, contacts, or other sensitive details?
Another effective strategy is to practice digital minimalism. This means intentionally reducing the amount of personal information shared online. For instance, think carefully before signing up for new services that require extensive personal data. Often, alternatives exist that require less information.
Regularly updating passwords and utilizing unique combinations can also strengthen defenses against unauthorized access. Password managers can help in this aspect, generating robust credentials that are difficult to crack. Regularly changing passwords further enhances security measures.
Additionally, enable two-factor authentication whenever possible. This extra step can significantly lower chances of breaches. While it may seem inconvenient at times, the benefits far outweigh the hassle. Being proactive about protective measures empowers individuals to maintain greater control over their online presence. In the end, a conscious approach to information sharing leads to a more secure digital experience.
